Recently a Nigerian medicine student called Chidiebere Ibe published his anatomical drawing of a pregnant black woman on his twitter page. It went viral, and was immediately picked up—rightly so—by the international press. Ibe correctly observed that darker skinned people are very much underrepresented (if indeed represented at all) in anatomical illustrations.
He definitely has a point. However, there is on aspect of his drawing that I believe could do with improvement. See Ibe’s drawing below.
Note the area around the genitalia. The illustration shows a cross section right down the middle, the midsaggital plane. It’s reasonably detailed too. You can see veins in blue, arteries in red, both small and large. Cross sectional views of the urethra, vagina and rectum are all fully in the picture, so we are certainly looking at the midsaggital plane. But then what happened to the external bit of the clitoris? See the image below for comparison.
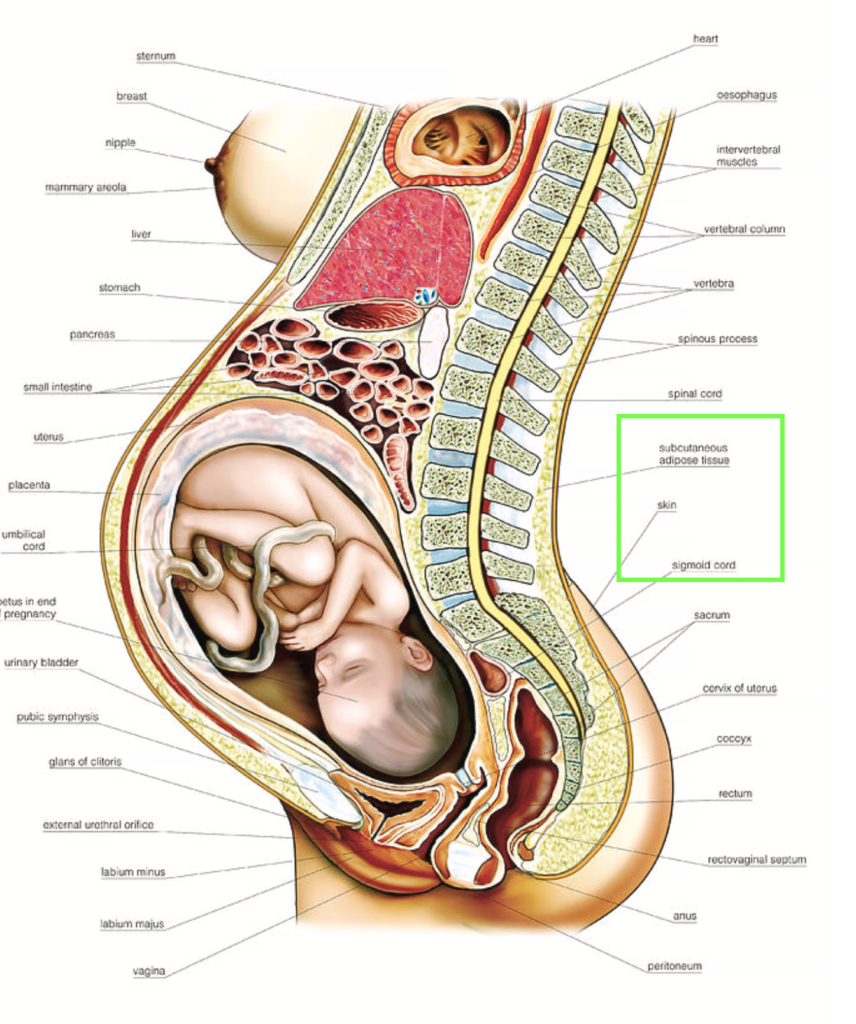
Compare the two illustrations. Disregarding the more cropped view of Ibe’s drawing, I cannot help but question why he drew everything else in that area quite detailed, but then went for what appears to be a partial clitorydectomy.
Whether or not the glans clitoris was intentionally omitted—for example because he considered it irrelevant—I do not know. Strange nonetheless that he did include the internal bit of the clitoris. Considering the fact that in Nigeria the occurrence of female genital mutilation, only made illegal as recent as 2015, remains very high, messing with the genitalia in an illustration that—given Ibe’s rise to fame—is probably also destined for e.g. Nigerian medical textbooks, is not advisable. Did Ibe consider that possibility? Probably not; he understandably seems overwhelmed by all the attention (and that attention, I hasten to reiterate, is still well deserved).
Regardless of Ibe’s motivation, any anatomical illustration, regardless of skin tone, should prominently include the important structures of the genitalia as visible and detailed as any other adjacent/related/relevant structure visible in that aspect of the cross section. Female genital mutilation (FGM) is universally regarded as a fundamental violation of human rights. The disgusting practice of FGM still happens, despite the ban, and that is really what makes this a bit of a sensitive issue. Ignoring that would be simply naive. In my humble opinion, an anatomical illustration should take that into account, where appropriate. For that reason, I would’ve thrown in some extra large labia in there as well, just to err on the side of caution. By the by, I would also frown on any standard medical illustration depicting a circumcised penis. That’s just my opinion: a standard anatomical illustration of the body must be shown naturally, without piercings, circumcisions, implants, tattoos, or any of that. Unless of course explicitly intended for illustrating a medical procedure, for example.
Other than that, I think Ibe’s drawing is a beautiful and very much needed addition to human anatomical illustrations. And I’m certain he didn’t deliberately intend to reflect FGM in his illustration, nor that he was trying to make the picture ‘modest’ in some way for cultural or religious reasons, or whatever. If he just includes at least the same level of details of the genitalia that he dedicated to, for example, the anus and urethra, then you’d really have a perfect picture. Then I believe it would truly be an even more splendid, and more than textbook worthy, illustration than it already is.












